Security & Compliance
Our specialized expertise in identity management, cloud-native security, and automation enables mid-sized enterprises to implement comprehensive security frameworks that protect critical assets while enabling business agility and innovation.
Identity & Access Management
We design and implement modern identity solutions that enforce least-privilege access while maintaining operational efficiency. Our certified security architects deliver:
- Zero-trust implementation frameworks that secure hybrid and multi-cloud environments
- Identity governance solutions that streamline access management and compliance reporting
- Privileged access management strategies that protect critical infrastructure components
- Multi-factor authentication architectures tailored for enterprise applications and systems
- Identity lifecycle automation that reduces operational overhead and security gaps
Container & Cloud-Native Security
Our container security specialists bring extensive experience implementing defense-in-depth strategies for modern application platforms while enabling DevSecOps practices. Our expertise includes:
- Kubernetes security frameworks incorporating network policies and admission controllers
- Container image security with vulnerability scanning and Software Bill of Materials (SBOM)
- Supply chain security strategies that protect the entire development lifecycle
- Runtime protection implementations that detect and prevent container-based attacks
- Cloud-native security operations models that integrate with enterprise security programs
Secrets Management
We implement comprehensive secrets management solutions that protect sensitive credentials, encryption keys, and configuration data across your entire technology stack. Our certified security experts deliver:
- Centralized secrets vault architectures that eliminate hard-coded credentials and configuration secrets
- Dynamic credentials solutions with automated rotation and just-in-time access
- Secure CI/CD pipeline integration for protecting sensitive build and deployment secrets
- Kubernetes secrets management that secures containerized application credentials
- Secrets lifecycle automation that reduces operational overhead and security gaps

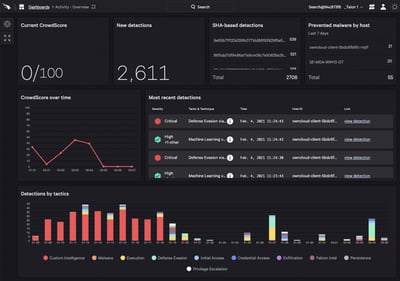
Security & Compliance Automation
We transform manual security and compliance processes into automated workflows that improve consistency, reduce response times, and strengthen your overall security posture while maintaining continuous regulatory compliance. Our automation specialists deliver:
- Security orchestration platforms that streamline incident response and remediation processes
- Compliance as Code frameworks that codify regulatory requirements into automated controls
- Automated vulnerability management systems that prioritize remediation efforts based on risk
- Continuous compliance monitoring that provides real-time validation of security controls
- Evidence collection automation that streamlines audit preparation and response
- Security as Code methodologies that embed security controls into infrastructure deployments
- Automated threat detection frameworks that leverage behavior analytics and machine learning
“Shadow-Soft has a fantastic reputation in the open-source community. Shadow-Soft’s work was foundational to what we’ve done architecturally since. As we continue to do test, probe and analyze the solution, Shadow-Soft’s recommendations help to keep us on track.”
 Josh BregmanFormer VP of Technology, CyGlass
Josh BregmanFormer VP of Technology, CyGlass
The Shadow-Soft Difference
Technical Leadership
Our leadership team will partner with you to make your vision a reality, providing strategic advice every step of your journey.
Technical Excellence
We maintain deep technical expertise through our team of certified professionals, including cloud native and Kubernetes security specialists, Red Hat Certified engineers, and cloud-platform certified architects who continuously upgrade their skills.
End-to-End Delivery Model
From assessment to implementation to team enablement, we provide comprehensive services that ensure successful outcomes at every stage.
Security Partners



What Our Partners Say
"Shadow-Soft's inclusion in the Partner Practice Accelerator program is exciting. Their expertise in automation and application modernization will be invaluable to enterprises leveraging Red Hat technologies. This collaboration enables us to provide commercial customers with the solutions and support they need to successfully adopt Red Hat OpenShift and Red Hat Ansible Automation Platform."
 Richard SimeoneEast Commercial Sales Leader at Red Hat
Richard SimeoneEast Commercial Sales Leader at Red Hat
News and Resources
Securing Kubernetes: A Guide For Security Leaders
Kubernetes is a Software Defined Datacenter for Containerized workloads, providing solutions for dynamically scaling workloads across Linux systems. You can secure your Kubernetes environment by understanding its core functionality, considering security concerns with the "4 C's" framework.
Shadow-Soft 4C's Security Framework
This framework focuses on the 4 C’s of Kubernetes Security: Cloud, Containers, Clusters, Code. Pay attention to how secrets, data clusters, authentication and authorization are handled.
Security & Compliance Client Stories
$600m Enterprise SaaS Platform Upgrades From Stand-Alone Keycloak to Kubernetes-Based Deployment, Reducing Load Time By 83.33%
Upgraded an enterprise SaaS platform's Keycloak from stand-alone to Kubernetes-based, enhancing performance by reducing load time by 83.33% and improving scalability.
Healthcare Platform Migrates Keycloak Instance In 2 Weeks
Faced with a legal request, this healthcare platform needed to reconfigure its Keycloak instance within two weeks while minimizing partner network disruption.
Let's Talk
How can we help? Tell us more about your project.




